Event Viewer enables you to view events and logs on your computer. And troubleshooting an issue might require to view log files from other remote computers. Event Log Subscriptions comes into play … Subscription enables you to save events from remote computers. In this article I am going to configure a collector and a target system.
Suppose you want to collect event log events from your domain controller on your client computer. Therefore your client computer is the collector und your domain controller is the target.
Client Computer (Collector)
Log on to your client computer (Windows Vista and above) with an account which is member of the domain admins group. Open Windows PowerShell and type wecutil qc. Hit enter.
wecutil qc
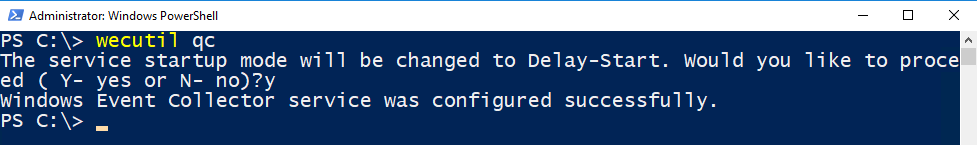
This will start the Event Collector Service.
Server Computer (Target System)
On Windows Server 2012 and 2016 Remote Management is enabled by default. Just to make sure it’s enabled, type
Configure-SMRemoting.exe -GET

If Remoting is not enabled you can simply enable it by running
Configure-SMRemoting.exe -ENABLE

Before we go to the next step open Server-Manager and make sure Remote Management is set to Enabled.

Now we have to add the collector’s computer account to the server’s Event Log Reader Group. You can do it either in cmd or PowerShell.
Add-ADGroupMember -Identity "Event Log Readers" -Members "client01$"

net localgroup "Event Log Readers" sid-500\client01$ /add

This will add client01 to the Event Log Readers Group. We are now ready to configure the main part.
Configuring Event Log Subscriptions
Log on to your collector computer (Windows 10). Open Event Viewer (eventvwr). Click Subscriptions and select Create Subscription.

Enter a Subscription Name and click on Select Computers.
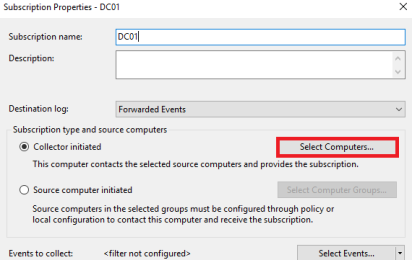
Click Add Domain Computers and type the computer name of your target system. It makes sense to test the connection before continue.
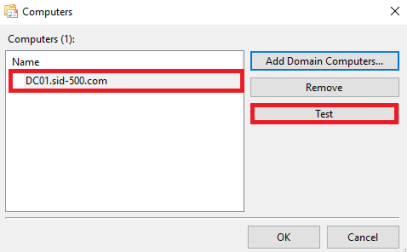

Next click Select Events.

Define a Query Filter. Select the events you want to collect.

Click OK.
Testing the functionality of Event Log Subscriptions
Wait a few minutes and do something on your target system. For example, restart the computer to trigger event log entries. Then go back to your client system and click on Windows Logs. Select Forwarding Events and review the logs of your target computer.
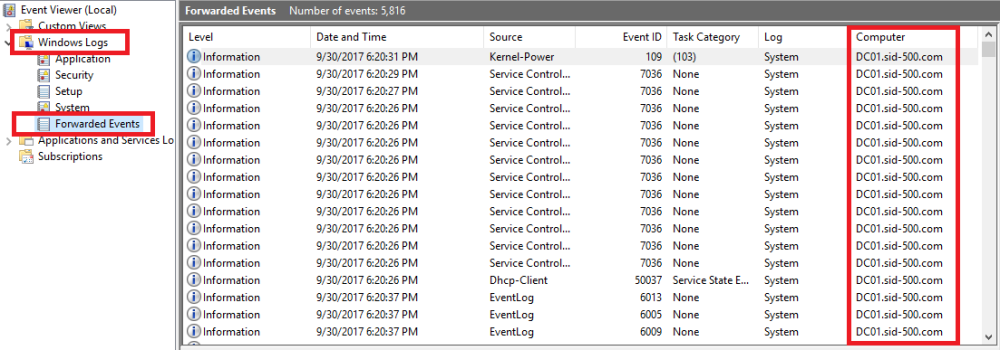
Nice. This completes the forwarding configuration.
Configure Advanced Settings
But there’s more. You can configure Bandwith, Latency and more … Go back to your recently configured subscription and double-click on it. Select Advanced.

Pay attention to the Event Delivery Optimization.
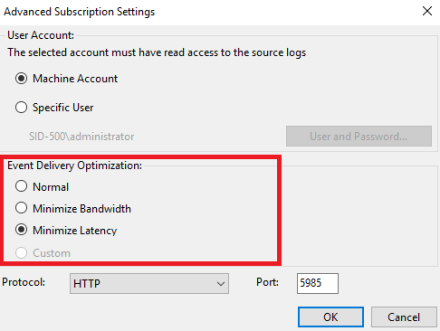
Using normal mode 5 items at a time are delivered. It’s a bit tricky to find a suitable setting that meets your requirement. I recommend reading the Official Microsoft article:
https://technet.microsoft.com/en-us/library/cc749167%28v=ws.11%29.aspx?f=255&MSPPError=-2147217396
Have fun playing with Event Log Subscriptions!
Categories: Cyber Security, Windows Server






Hi Patrick,
Thank you for your interesteing blog, just a short question, how can I send emails from subscriptions when some Event Log ocurr?
Regards
Tom
LikeLike
How does one configure server core as an event collector? Or, put another way; how do I configure an event log subscription in powershell?
I’ve been asked to forward all domain server security logs to a central collector machine, and the boss wants the collector machine as server core 2019.
LikeLike
I know this is a few years old, but i have a question.
Is there any way to script the computer names into the subscription on the WEF server itself?
We want to create an automated process that adds computers to those without having to do it manually.
LikeLike
Wow, that blows my mind. I don’t know, man. Tip: You can get all computer names with Get-ADComputer.
LikeLike