In this blog post I am going to describe how to use PowerShell to administer Group Polices in your Active Directory environment. Group Polices control the environment of users and computers. But it´s not just controlling: Goup Polices can help you to make your client and server systems more user-friendly.
The Module Group Policy
All commands can be found in the module Group Policy. Simply run Get-Command on one of your Domain Controllers to get them all.
Get-Command -Module GroupPolicy

Create a GPO
First, we create a simple Group Policy Object without any configuration.
New-GPO -Name "ScreenSaverTimeOut" -Comment "Sets the time to 900 seconds"

Configure the GPO Screensaver Timeout
And now the bad news: You have to enter a registry key.
Set-GPRegistryValue -Name "ScreenSaverTimeOut" -Key "HKCU\Software\Policies\Microsoft\Windows\Control Panel\Desktop" -ValueName ScreenSaveTimeOut -Type String -Value 900
Link the GPO to an Organizational Unit / Domain / Site
Now we have configured a GPO. The last step is to link it to an Active Directory Object (OU, Domain, Site).
New-GPLink -Name "ScreenSaverTimeOut" -Target "ou=people,dc=pagr,dc=inet"

As you can see it´s not enforced by default. Enforcing a GPO is a very rare configuration. It can be useful when some of our Organizational Units are configured to block inherited GPOs from parent OUs. Then the enforced GPO will override those setting. More about it later.
Review your GPO
You can check your previous configured GPO by using the graphical interface or PowerShell.
Get-GPO -Name "ScreenSaverTimeOut" | Get-GPOReport -ReportType HTML -Path $Home\report.html Invoke-Item $Home\report.html

Or open gpmc.msc and navigate to the object.

Configure Advanced Settings
Inherited Group Policies
To find all inherited Group Policy Objects for an Organizational Unit, run
Get-GPInheritance -Target "ou=people,dc=pagr,dc=inet"

Blocking inheritance
If you want to block all GPOs inherited from parent Organizational Units, run
Set-GPInheritance -Target "ou=people,dc=pagr,dc=inet" -IsBlocked 1

Compare this screenshot to the previous. The Default Domain Policy comes from a parent object and is now gone.
Enforcing Group Policies
As mentioned earlier, enforcing overrides blocking. So, if I enforce my Default Domain Policy, it should be there again.
Set-GPLink -Name "Default Domain Policy" -Target "dc=pagr,dc=inet" -Enforced Yes

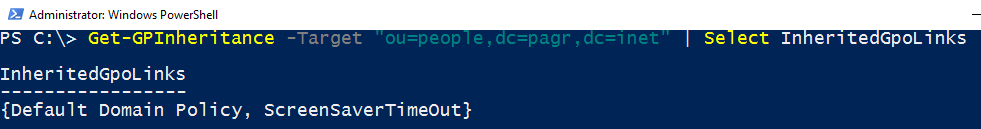
And it´s there again:
Get-GPInheritance -Target "ou=people,dc=pagr,dc=inet" | Select InheritedGpoLinks
Configure Security Settings
The default security setting for all newly created GPOs is Authenticated Users (Apply). This means, that all objects in an OU, Site or Domain, where the policy is applied to, have the right to read the GPO and therefore to apply it.
For example, you have 10 users in an OU. You want to apply a GPO to one user only. Then simply modify the rights of the Authenticated Users group.

To do that, remove the authenticated users group. Don´t care about the warnings.
Set-GPPermission -Name "ScreenSaverTimeOut" -TargetName "Authenticated Users" -TargetType User -PermissionLevel None
Then add it again. But now allow only “Read”.
Set-GPPermission -Name "ScreenSaverTimeOut" -TargetName "Authenticated Users" -TargetType User -PermissionLevel GPORead
And finally, add your user and grant the user “GPOApply”.
Set-GPPermission -Name "ScreenSaverTimeOut" -TargetName "Petra" -TargetType User -PermissionLevel GPOApply

See also
PowerShell: Force gpupdate on all Domain Computers
Categories: PowerShell, Windows Server






Hi, I believe your example is copied from Microsoft’s example here: https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/ee461034(v%3dtechnet.10)
and the problem is: it doesn’t work. Both report.html and the GPO say “Display names for some settings cannot be found. You might be able to resolve this issue by updating the .ADM files used by Group Policy Management”
Well, thanks to https://www.verboon.info/2010/10/creating-group-policy-objects-with-powershell/ we have the answer:
“Microsoft has used the ScreenSaveTimeOut setting in their CmdLet example which has a typo, the example shows Dword but it must be String.”
Change from Dword to String and it works happily.
Enjoy!
LikeLike