Have you always dreamed of fine-tuning permissions? PowerShell JEA makes it possible. The user only sees what he should see and can only do what he should do. With a few simple steps everything is ready. Let’s dive in.
What is JEA (Just-Enough-Administration)?
The main purpose of JEA is to limit privileges. We can specify what a user can do on a very granular basis. For example you want to restrict a user to restart the spooler service only, then go for JEA. Unfortunately, this only works with PowerShell. So for the following keep in mind, that the target user should not work with PowerShell for the first time.
What’s in this article?
In this article I will restrict the Active Directory user petra to running only Restart- Service spooler and whoami on DC01. For this I will use a Windows Server 2016 (DC01) that is configured as an Active Directory Domaincontroller for sid-500.com. Additionally, I will use a Windows 10 Workstation that is joined to the Domain sid-500.com. All tests are performed from this computer.
The article is divided into 4 steps:
- Creating a PS Session Configuration File
- Creating a folder for JEA
- Creating a Capability File
- Registering the Configuration
And finally Petra’s test. I think it’s time to get started now.
Creating a PS Session Configuration File for the Spooler Admins Group (pssc file)
It’s better if we create the file right away and talk about it later – if it’s already there. Sometimes it makes more sense to do the exercise first and then talk about what we are doing. 😉 And as usual on my blog – everything with screenshots.
I’m logged on my Domain Controller DC01.
New-PSSessionConfigurationFile -Path 'C:\Program Files\WindowsPowerShell\spooler_conf.pssc'

What have we done now? A default file has been created. Let’s look into this file.
notepad 'C:\Program Files\WindowsPowerShell\spooler_conf.pssc'

In this file you can specify whether everything is to be logged and for which users or groups your configuration is to be made available. For changes remove the # from the lines.
My goal is that only users that are member of the Spooler_Admins group can restart the spooler service and run whoami. That means that I have to modify this file.
First I change the author. Unspectacular.

Then I change the Session Type to RestrictedRemoteServer. This allows the execution of the following commands: Exit-PSSession, Get-Command, Get-FormatData, Get-Help, Measure-Object, Out-Default, and Select-Object.

Afterwards I specify a logging folder (all user sessions will be logged in this folder with PowerShell transaction logging) and I activate the RunAsVirtualAccount feature (optional). If a user logs in the this user works with a temporary virtual account.
Make sure the Transcript Directory exists!

Now we come to the most important part: Specifying the name of the Capability setting.

Note that the name of the RoleCapabilities must match the file name in the third part.
Save the file and close it.
Creating a folder for JEA
In this part we create a folder for the JEA configuration file that will be used in the next part.
New-Item -Path 'C:\Program Files\WindowsPowerShell\Modules\JEA\RoleCapabilities' -ItemType Directory

That’s it for this section.
Creating the PS Role Capability File for the Spooler Admins (psrc file)
This is the most interesting part. Here we configure what they are allowed to do. It’s important that you name this file spooler_admins. Remember we have configured the session configuration file to the role capabilities = spooler_admins!
New-PSRoleCapabilityFile -Path 'C:\Program Files\WindowsPowerShell\Modules\JEA\RoleCapabilities\spooler_admins.psrc'

Next open the file.
notepad 'C:\Program Files\WindowsPowerShell\Modules\JEA\RoleCapabilities\spooler_admins.psrc'

Feel free to change the author, description and more. I’ll concentrate on the most important setting. We want to restrict the Spooler Admins that they can only run Restart-Service and the whoami command. For this I have to modify the Cmdlets section to make the appropriate command visible for the Spooler Admins group.

Next I want to allow running whoami. Whoami is not a cmdlet, but an external command.

That’s it. Save the file and close it.
Registering the Configuration
Finally, we have to activate it. Choose a name and enter the path to the config file. Make sure, that the group already exists!

Register-PSSessionConfiguration -Name Spooler_Admins -Path 'C:\Program Files\WindowsPowerShell\spooler_conf.pssc'

Readers know more. We have to restart the Windows Remote Management Service.
Restart-Service WinRM
We’re done. Now the test is coming up.
Testing the configuration
User petra is logged on a Windows 10 Computer that is joined to my domain. Remember that petra is member of the spooler_admins group. Let’s start.
Petra tries to log in via a PowerShell Remote Session. In order to to this, she has to specify the configuration name.
Enter-PSSession -ComputerName dc01 -ConfigurationName spooler_admins
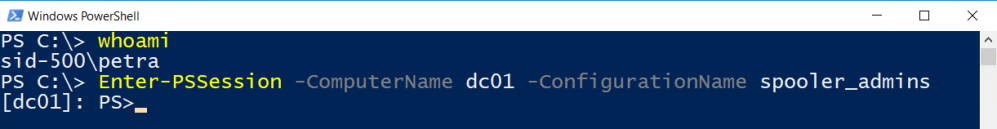
Surprise … surprise she’s in. But what is she allowed to do? Nice the Restart-Service is there.

and the spooler restart works …

Is she allowed to restart any other service? Nope.

She should be able to run whoami …

We’ve configured a transcription log … located at C:\Transcripts …

That’s it. We’re done.
Conclusion
The only disadvantage of this nice security feature is that everything has to be done in PowerShell. As I have already mentioned in one of my contributions, my teaching experience is that 7/10 are still unfamiliar with PowerShell. Time to change it. 😉
Hope this was helpful and interesting.
Categories: PowerShell, Windows Server






Excellent walk-through, Patrick!
I am running into the following when trying to register my .pssc file when I include the optional RunAsVirtualAccount = $true
Enter-PSSession: Connecting to remote server SERVER01 failed with the following error message : For more information, see the about_Remote_Troubleshooting Help topic.
Almost nothing on the web about this message code.
Any pointers?
LikeLike
Sheeesh! Pasted the wrong output
The error is:
New-Item:
Line |
81 | new-item -path WSMan:\localhost\Plugin -file “$filepath” .
| ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
| The configuration XML is not valid. Either attribute: “RunAsVirtualAccount” is not expected for element: “PlugInConfiguration” or its namespace is invalid.
LikeLike
Although I had installed PowerShell 7 on my Server 2012 R2 box I found that I also needed to update Windows Management Framework on the server as well. Once I’d done that I was immediately able to register the .pssc file without error and subsequently connect from a client machine. Thank you Sir!
LikeLike
Thank you for the kind words!
LikeLike
Great article, thank you!
What is the best approach to implement JEA at scale? say on 1000s of servers?
The way I see it:
1. GPO Add user/users to a “Remote Management Users” group, otherwise a non-admin user cannot create PS sessions
2. GPO create JEA folders (ie RoleCapabilities)
3. GPO deliver files (psrc, pssc)
4. GPO run a one off command to register JEA configuration?
4a. Possibly restart WinRM service
How do you do it?
LikeLike
Thank you for the great comment! Looks good. Unfortunately, I have no experience in implementing jea in large environments. Here in Austria there are only tiny companies 😉
LikeLike
Haha. Thank you for the response!
I decided to plan the deployment with Saltstack as it is a lot more flexible. Still in the testing phase.
LikeLiked by 1 person
Great article, many thanks
LikeLike
Thank you!
LikeLike
Hi!
Thank you for your kind words.
1) You can provide your scripts as an external command in the psrc file (see above). It’s similar to my whoami example in the article.
2) Yes, I’ve implemented this in one of my environments. Install PowerShell Web Access (see my article) and provide them a Web Interface! They can then access your scripts from every device in form of a Web Interface.
All the best,
P
LikeLike
Partick –
I love this walk through. Although, I can’t get my head around 2 things.
1) How would I configure this to have a group of help desk peeps run a few scripts I created for them.
Is there a directory these scripts need to be in?
Is there a configuration item i need to add to the conf file?
Will there be any issues if the scripts are remote-ing into other machines?
2) How do I deliver/present the powershell console to a user whom I’m not sure if they’ll have the rights to start a pssession remotely.
Will these peeps need access to the Server?
Any alternatives if they aren’t able to access the server through WinRm pssession
LikeLiked by 1 person